
| Quarter | Attacks Detected Millions |
|---|---|
| Q1 2025 | 1 |
| Q2 2025 | 1.2 |
| Q3 2025 | 1.2 |
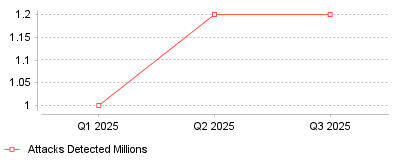
Recent industry reports indicate a significant shift in mobile security dynamics, where iOS devices have surpassed Android in phishing exposure rates within enterprise environments. Specifically, 2024 data shows that 26% of enterprise iOS devices were targeted by phishing attacks, compared to only 12% of Android devices [1]. Furthermore, the volume of these social engineering attacks is escalating, with enterprise-focused mobile phishing incidents exceeding 1.2 million per quarter throughout mid-to-late 2025 [2].
For the Mobile Device Management (MDM) industry, this data represents a tactical pivot from "device-centric" security to "identity-centric" threats. Historically, MDM software focused on locking down Android devices against malware and sideloaded apps, viewing iOS as the inherently safer "walled garden." However, the data suggests that cybercriminals have largely abandoned trying to hack the robust iOS kernel and are instead hacking the user through SMS, WhatsApp, and QR codes to steal login credentials [3]. This means that traditional MDM policies—such as enforcing passcodes or restricting app stores—are no longer sufficient, as they cannot stop a user from voluntarily handing over credentials on a phishing site. This trend necessitates the integration of Mobile Threat Defense (MTD) capabilities directly into MDM agents to scan network traffic and links rather than just managing device settings.
This trend is critical because iOS devices are disproportionately used by high-value targets, such as executives and government officials, who have elevated access to sensitive corporate data [2]. A successful phishing attack on a C-suite executive's iPhone can lead to a "Business Email Compromise" (BEC) or a breach of cloud infrastructure that bypasses traditional perimeter defenses. Furthermore, 82% of phishing sites are now specifically adapted for mobile devices, making them harder to detect on smaller screens where URL bars are often hidden [4].
The disparity likely stems from the difficulty of compromising iOS via traditional malware; because the operating system is so secure, attackers are forced to rely on social engineering, which is OS-agnostic [1]. Additionally, the user demographic for iOS in the enterprise often includes decision-makers who are frequently targeted by "whaling" campaigns (high-level phishing). Speculatively, the user interface of iOS, which prioritizes a seamless user experience, may sometimes obscure full URLs or security certificates more aggressively than Android, or users may simply have a false sense of security believing their iPhones are invulnerable to attack.
The data confirms that the era of relying solely on an operating system's native security is over; the "human factor" is now the primary vulnerability in the mobile stack. Organizations must update their MDM strategies to include real-time anti-phishing protection that works across all apps, not just corporate email. The prominent takeaway is that while iPhones may be harder to infect with a virus, they are currently twice as likely to be the conduit for a credential theft attack [1].
The operational landscape of Mobile Device Management (MDM) has shifted rapidly from simple asset tracking to a complex convergence of cybersecurity, user privacy, and autonomous remediation. As organizations face a perimeter-less workforce, the traditional models of reactive device management are failing to keep pace with the volume and sophistication of modern threats. In 2025, the proliferation of endpoints—ranging from smartphones and laptops to IoT sensors—has forced a transition from standalone MDM to Unified Endpoint Management (UEM), driven by the necessity to secure diverse operating systems under a single pane of glass.
Current research indicates that unmanaged devices represent a critical vulnerability gap. According to the 2025 Verizon Data Breach Investigations Report, the exploitation of vulnerabilities as an initial access vector has grown significantly, reaching 20% of analyzed breaches, while non-managed devices accounted for 46% of compromised systems with corporate credentials [1]. Consequently, IT leaders are no longer viewing MDM solely as an administrative tool but as a foundational layer of their Cybersecurity, Privacy & Compliance Software stack.
This report analyzes the prevailing trends reshaping device management, the operational friction points challenging IT departments, and the specific implications for high-turnover and high-compliance industries. It explores how granular controls, such as Apple’s Declarative Device Management and Android 15’s Private Space, are redefining the balance between corporate security and user privacy.
The global MDM and UEM market is experiencing robust growth, driven by the permanent adoption of hybrid work models and the expansion of the Internet of Things (IoT). Market analysis suggests that the Unified Endpoint Management market size is projected to grow from approximately $15.45 billion in 2025 to over $146 billion by 2033, expanding at a CAGR of 32.5% [2]. This growth is not merely in volume but in functional scope.
Modern Mobile Device Management (MDM) Software is increasingly indistinguishable from endpoint security platforms. The historical separation between management (provisioning, configuration) and security (threat defense, access control) has dissolved. This convergence is driven by the "Zero Trust" architecture, where device health and compliance status are real-time prerequisites for accessing corporate resources. As noted in recent industry assessments, UEM platforms are now evaluated on their ability to integrate with identity management and security information and event management (SIEM) systems to provide a holistic defense posture [3].
A defining trend in 2024 and 2025 is the shift from server-based polling to device-driven autonomy. Traditional MDM relied on the server periodically checking the device status—a process that is bandwidth-intensive and latent. The new paradigm, led by Apple’s Declarative Device Management (DDM) and similar protocols, allows devices to proactively apply logic and report status changes without waiting for server commands. This shift is critical for maintaining compliance in real-time, ensuring that a device that falls out of compliance (e.g., disables a passcode) is immediately remediated or quarantined [4].
Apple’s transition to DDM represents the most significant architectural change in device management in a decade. By moving logic to the client side, devices can autonomously react to state changes. For 2025, this includes new capabilities for software update management, allowing IT administrators to enforce update deadlines and deferrals with greater precision [5]. This evolution reduces the load on MDM servers and ensures that security patches are applied faster, closing the window of vulnerability that attackers often exploit.
On the Android front, the release of Android 15 has introduced "Private Space," a feature that creates a separate, locked container for sensitive apps within the personal profile. For enterprise environments, this complicates the Bring Your Own Device (BYOD) landscape but offers opportunities for better privacy delineation. Crucially, Android 15 allows IT admins to extend personal app policies to this private space on company-owned devices, ensuring that even "hidden" areas of a corporate device remain compliant [6]. Furthermore, theft detection locks utilizing AI to detect snatching motions add a physical layer of security to the software stack [7].
Artificial Intelligence is permeating MDM workflows to address the skills gap in IT. Modern platforms now utilize AI to analyze telemetry data for anomaly detection—identifying devices that deviate from normal behavior patterns which may indicate a compromise. Beyond detection, AI enables "self-healing" capabilities, where common issues like failed application installs or configuration drifts are automatically remediated without human intervention. This automation is essential for scaling operations without proportionally increasing IT headcount [8].
Despite these technological advancements, operational teams face significant hurdles. The primary challenge is complexity: managing a heterogeneous fleet of iOS, Android, Windows, macOS, and Linux devices, each with different update cycles and management APIs.
The debate between Bring Your Own Device (BYOD) and Corporate-Owned, Personally Enabled (COPE) models continues to strain IT policies. While BYOD reduces hardware costs, it introduces "Shadow IT" risks where personal apps compromise corporate data. Research shows that 46% of compromised devices with corporate logins are non-managed, highlighting the severe risk of BYOD implementations that lack robust containerization [9].
Conversely, COPE models provide greater security control but require higher capital expenditure and privacy management. The trend in 2025 is shifting toward COPE for knowledge workers to ensure data sovereignty, while BYOD remains prevalent for contractors and gig workers, albeit with stricter enrollment requirements like User Enrollment or Android Work Profiles [10].
For industries with high employee turnover, the logistics of issuing, securing, wiping, and retrieving devices is a massive operational drain. Data indicates that managing mobile inventory and reverse logistics are among the top challenges for IT teams, with 70% of companies struggling to manage mobile inventory effectively [11]. Failure to reclaim devices not only results in financial loss but also leaves corporate data exposed on hardware that has left the organization's physical control.
The impact of these trends varies significantly across different business verticals. The "one-size-fits-all" approach to MDM is obsolete; successful implementation requires tailoring the software to the specific operational tempo and risk profile of the industry.
Recruitment firms handle vast amounts of Personally Identifiable Information (PII). The operational challenge here is two-fold: securing recruiter devices that access applicant data and managing the devices deployed to temporary staff. The high velocity of staff onboarding and offboarding necessitates zero-touch enrollment and automated wiping capabilities. Mobile Device Management (MDM) Software for Recruitment Agencies must prioritize remote wipe functionalities and robust application blacklisting to prevent data exfiltration via unauthorized cloud storage or messaging apps. The risk of insider threats in this sector is elevated, making role-based access control (RBAC) enforced via MDM a critical requirement [12].
Similarly, general staffing firms face the logistical nightmare of managing assets for a transient workforce. Mobile Device Management (MDM) Software for Staffing Agencies focuses heavily on asset tracking and geofencing. If a device assigned to a temporary worker leaves a designated job site, the MDM must be capable of triggering an alert or automatically locking the device to prevent theft. This capability directly addresses the high costs associated with unrecovered hardware in high-turnover environments.
Contractors often operate outside the corporate firewall, frequently using their own devices (BYOD). The operational challenge is isolating corporate data from personal data without infringing on the contractor's privacy. Mobile Device Management (MDM) Software for Contractors increasingly relies on "containerization" technologies. This creates a secure enclave on the device for business applications. If the contract ends, the enterprise can wipe only the secure container, leaving the contractor’s personal photos and apps touched. This separation is vital for legal compliance and user acceptance in the gig economy [13].
For Private Equity firms, MDM is not just an operational tool but a component of risk assessment during Mergers and Acquisitions (M&A). Undisclosed cybersecurity vulnerabilities in a target company's mobile fleet can devalue a deal or lead to post-acquisition liabilities. Mobile Device Management (MDM) Software for Private Equity Firms is often used to audit the security posture of portfolio companies. Acquiring firms must assess if the target company has adequate visibility into its endpoints. A lack of managed devices often signals deeper "shadow IT" issues and regulatory non-compliance, which are red flags during due diligence [14].
Software-as-a-Service (SaaS) companies operate under immense pressure to maintain certifications like SOC 2 and ISO 27001 to win enterprise clients. Mobile Device Management (MDM) Software for SaaS Companies is essential for automated evidence collection. Auditors require proof that all employee workstations are encrypted, password-protected, and patched. Modern MDM platforms integrate with compliance automation tools (like Drata or Vanta) to provide continuous, automated evidence that satisfies auditor requirements, replacing manual screenshots and spreadsheet tracking [15].
The business case for advanced MDM adoption is driven by risk mitigation and operational efficiency. The cost of a data breach continues to rise, with healthcare and finance sectors seeing the highest per-record costs. However, the operational cost of *unmanaged* devices is equally damaging. IBM/Ponemon data suggests that the time to identify and contain breaches is significantly longer when remote workers and unmanaged devices are involved.
Beyond security, MDM impacts the Digital Employee Experience (DEX). A poorly configured MDM solution that drains battery life, slows down devices, or frequently interrupts users with update prompts leads to "security fatigue" and workarounds. Conversely, a well-tuned UEM strategy ensures that employees have the right apps and access immediately upon onboarding. In 2025, 87% of IT professionals reported that strong DEX positively affects employee productivity, making MDM a key driver of retention in a competitive labor market [16].
Looking ahead to 2026 and beyond, the MDM landscape will likely be defined by "Autonomous Endpoint Management" (AEM). Gartner predicts that by 2029, over 50% of organizations will adopt AEM capabilities to reduce human effort [17]. This will involve systems that not only patch themselves but also predict hardware failures and security breaches before they occur.
Furthermore, the integration of generative AI into MDM consoles will allow administrators to query their fleet using natural language (e.g., "Show me all iOS devices that haven't updated in 30 days and block them") rather than building complex SQL queries. As the perimeter dissolves completely, the device *is* the network, and MDM software will remain the primary control plane for enterprise security.