Best for teams that are
- Organizations wanting unbiased advice on selecting penetration testing vendors
- Companies needing to rotate vendors to avoid complacency in security testing
- Teams needing help defining the right scope for compliance mandates
Skip if
- Teams looking for a direct, immediate testing engagement without a middleman
- DIY users seeking a software tool to conduct their own scans
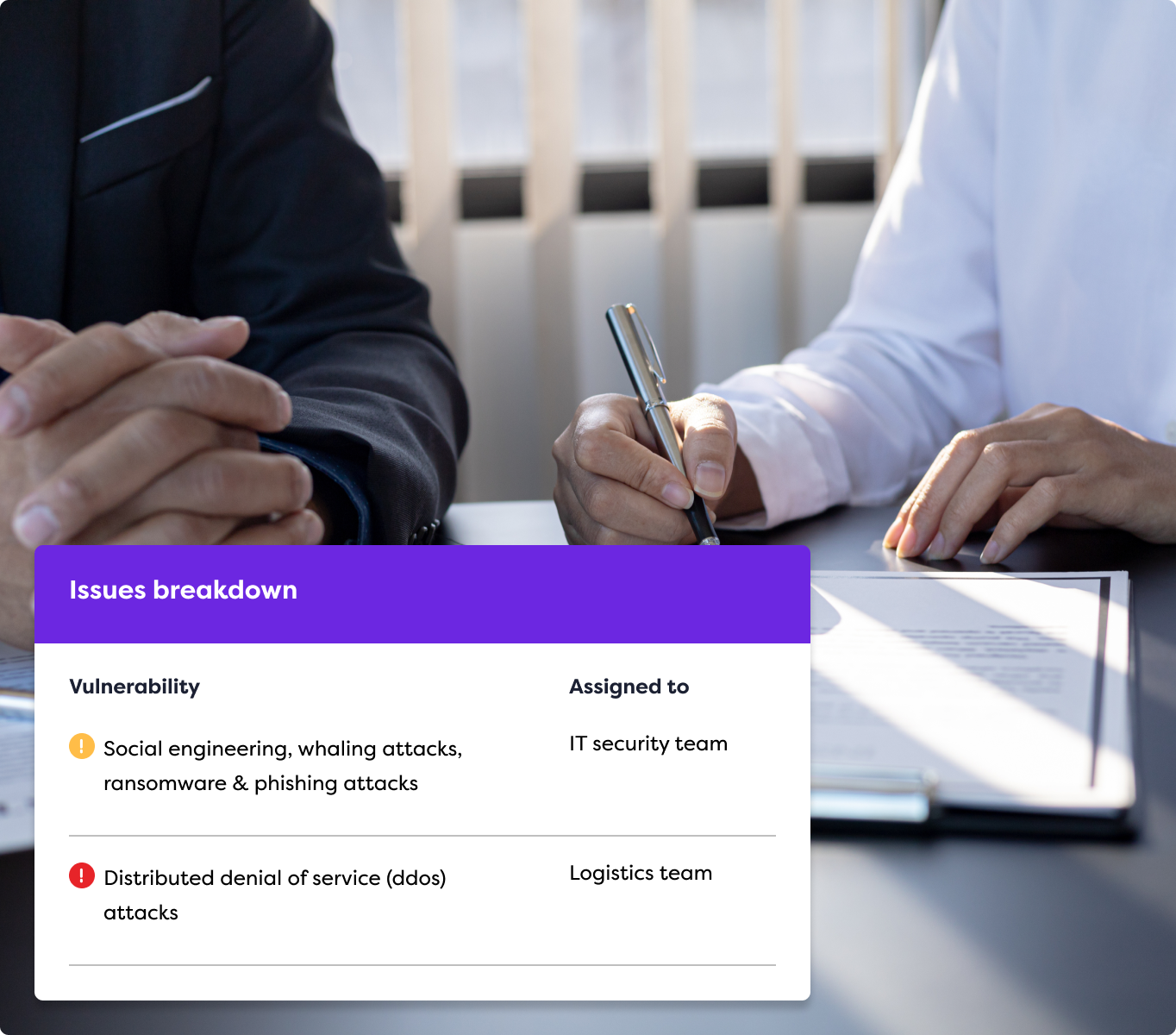
Expert Take
Our analysis shows VLCM stands out by acting as a strategic broker rather than a direct provider, leveraging a 'Vendor Rotation' strategy that prevents security blind spots caused by tester complacency. Research indicates they partner with elite firms like NetSPI and Rapid7, allowing clients to access top-tier ethical hackers without managing complex vendor relationships. Based on documented features, their 'Risk-Aligned Scoping' ensures organizations pay for the specific depth of testing required—whether for compliance or critical defense—rather than a generic, one-size-fits-all scan.
Pros
- Access to elite vendors (NetSPI, Rapid7)
- Managed vendor rotation strategy
- Risk-aligned scoping prevents overspending
- Transparent pricing ranges published
- Strong industry awards and credibility
Cons
- No in-house penetration testing team
- Reliance on third-party availability
- Variable pricing based on vendor
- Potential communication layer complexity
- Scheduling dependent on partner capacity