Why We Love It
AWS Identity and Access Management (IAM) is a favorite among industry professionals due to its robustness, security, and ability to scale. It gives granular control over AWS resources, allowing organizations to enforce security best practices seamlessly. With features like multi-factor authentication and identity federation, it provides an extra layer of security. Moreover, it's deeply integrated into the AWS ecosystem, making it a natural choice for businesses already leveraging AWS services.
Pros
- Advanced security features
- Scalable and flexible
- Easy integration with AWS ecosystem
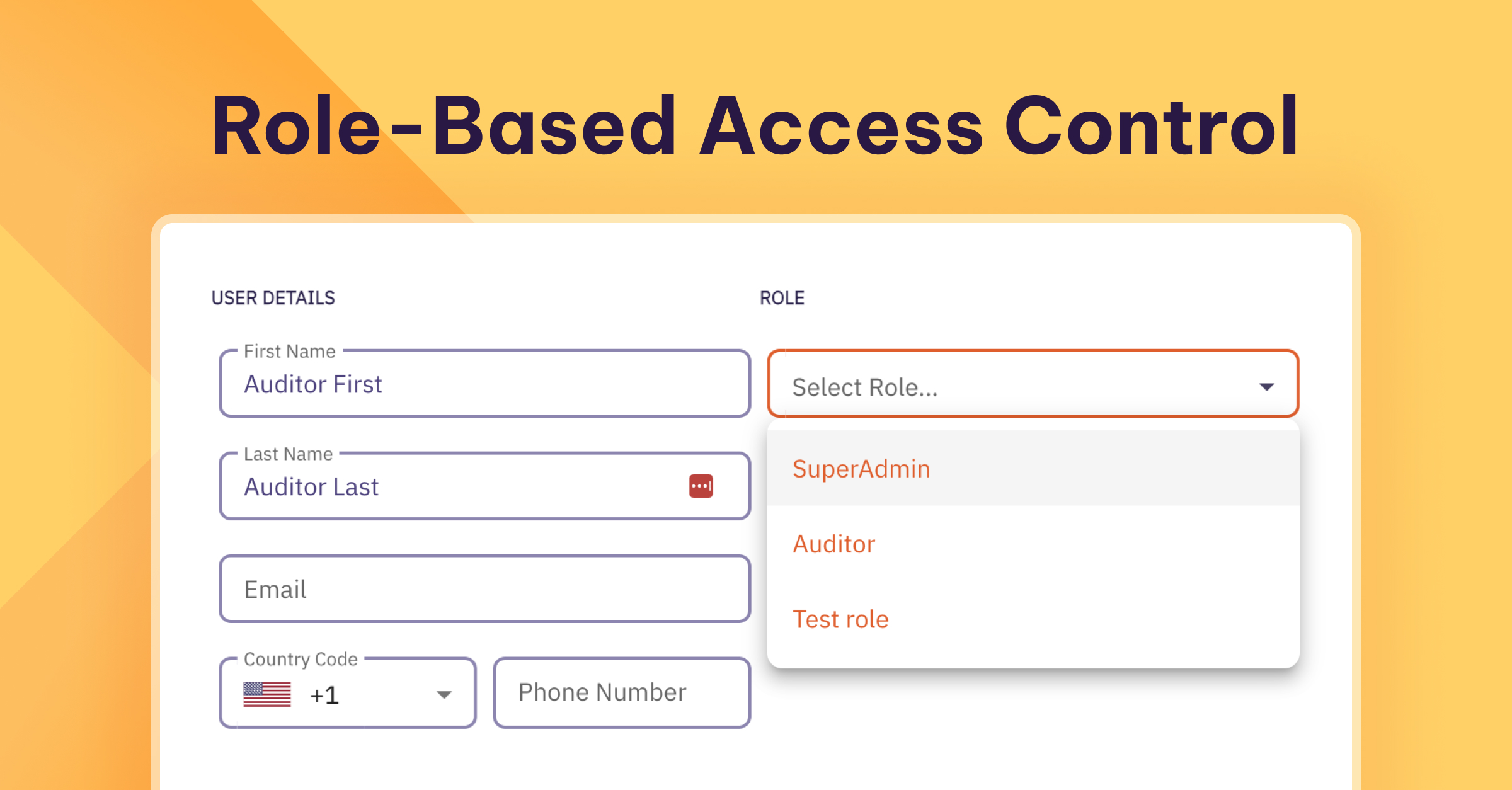
- Fine-grained access control
- Support for multi-factor authentication
Cons
- Complex setup process
- Requires knowledge of AWS ecosystem
- No flat-rate pricing
Pay for what you use pricing model
AWS Identity and Access Management (IAM) is a comprehensive and robust solution designed to help businesses manage and scale access to their workloads and workforce securely. It is specifically tailored for IT professionals in the industry who need a reliable, scalable, and secure IAM platform that supports agility, innovation, and simplifies the management of user access to AWS services and resources.
Pros
- Advanced security features
- Scalable and flexible
- Easy integration with AWS ecosystem
- Fine-grained access control
- Support for multi-factor authentication
Cons
- Complex setup process
- Requires knowledge of AWS ecosystem
- No flat-rate pricing
Why We Love It
AWS Identity and Access Management (IAM) is a favorite among industry professionals due to its robustness, security, and ability to scale. It gives granular control over AWS resources, allowing organizations to enforce security best practices seamlessly. With features like multi-factor authentication and identity federation, it provides an extra layer of security. Moreover, it's deeply integrated into the AWS ecosystem, making it a natural choice for businesses already leveraging AWS services.
Pros
- Advanced security features
- Scalable and flexible
- Easy integration with AWS ecosystem
- Fine-grained access control
- Support for multi-factor authentication
Cons
- Complex setup process
- Requires knowledge of AWS ecosystem
- No flat-rate pricing
Why We Love It
AWS Identity and Access Management (IAM) is a favorite among industry professionals due to its robustness, security, and ability to scale. It gives granular control over AWS resources, allowing organizations to enforce security best practices seamlessly. With features like multi-factor authentication and identity federation, it provides an extra layer of security. Moreover, it's deeply integrated into the AWS ecosystem, making it a natural choice for businesses already leveraging AWS services.
Pay for what you use pricing model
AWS Identity and Access Management (IAM) is a comprehensive and robust solution designed to help businesses manage and scale access to their workloads and workforce securely. It is specifically tailored for IT professionals in the industry who need a reliable, scalable, and secure IAM platform that supports agility, innovation, and simplifies the management of user access to AWS services and resources.