Why We Love It
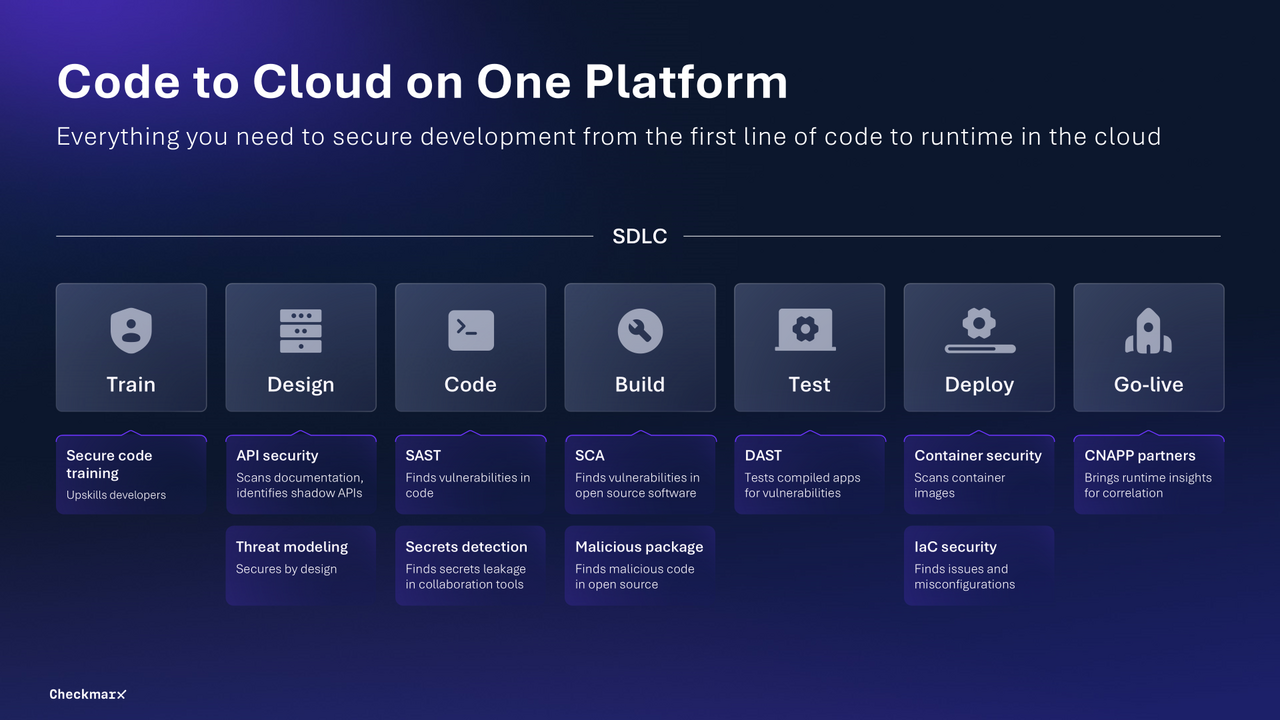
Snyk CI/CD Pipeline Security is a game changer for tech professionals, particularly those in software development and IT security. It integrates seamlessly with popular CI/CD tools, allowing for a smooth workflow. The proactive vulnerability management is a key feature, enabling developers to address security issues in real-time, which is vital in the fast-paced tech industry. Plus, its comprehensive security scanning tools ensure that no stone is left unturned when it comes to securing your CI/CD pipelines.
Pros
- Native integration with CI/CD tools
- Proactive vulnerability management
- Comprehensive security scanning capabilities
- CLI support
Cons
- Requires technical expertise
- No specific pricing details on website
Enterprise pricing available
Snyk CI/CD Pipeline Security is specifically designed to meet the needs of developers seeking robust security for continuous integration/continuous delivery pipelines. It's native integration with your favorite CI/CD tools and CLI, coupled with security scanning capabilities, allows for proactive vulnerability management, addressing the critical need for secure software delivery in the tech industry.
Pros
- Native integration with CI/CD tools
- Proactive vulnerability management
- Comprehensive security scanning capabilities
- CLI support
Cons
- Requires technical expertise
- No specific pricing details on website
Why We Love It
Snyk CI/CD Pipeline Security is a game changer for tech professionals, particularly those in software development and IT security. It integrates seamlessly with popular CI/CD tools, allowing for a smooth workflow. The proactive vulnerability management is a key feature, enabling developers to address security issues in real-time, which is vital in the fast-paced tech industry. Plus, its comprehensive security scanning tools ensure that no stone is left unturned when it comes to securing your CI/CD pipelines.
Pros
- Native integration with CI/CD tools
- Proactive vulnerability management
- Comprehensive security scanning capabilities
- CLI support
Cons
- Requires technical expertise
- No specific pricing details on website
Why We Love It
Snyk CI/CD Pipeline Security is a game changer for tech professionals, particularly those in software development and IT security. It integrates seamlessly with popular CI/CD tools, allowing for a smooth workflow. The proactive vulnerability management is a key feature, enabling developers to address security issues in real-time, which is vital in the fast-paced tech industry. Plus, its comprehensive security scanning tools ensure that no stone is left unturned when it comes to securing your CI/CD pipelines.
Enterprise pricing available
Snyk CI/CD Pipeline Security is specifically designed to meet the needs of developers seeking robust security for continuous integration/continuous delivery pipelines. It's native integration with your favorite CI/CD tools and CLI, coupled with security scanning capabilities, allows for proactive vulnerability management, addressing the critical need for secure software delivery in the tech industry.